Bots
A bot, in the most general sense, refers to an autonomous program designed to carry out pre-determined tasks over the internet. While the tasks run by bots are typically simple, over time these software programs have been developed to tackle increasingly complex things – both good and bad.
What are bots in mobile fraud?
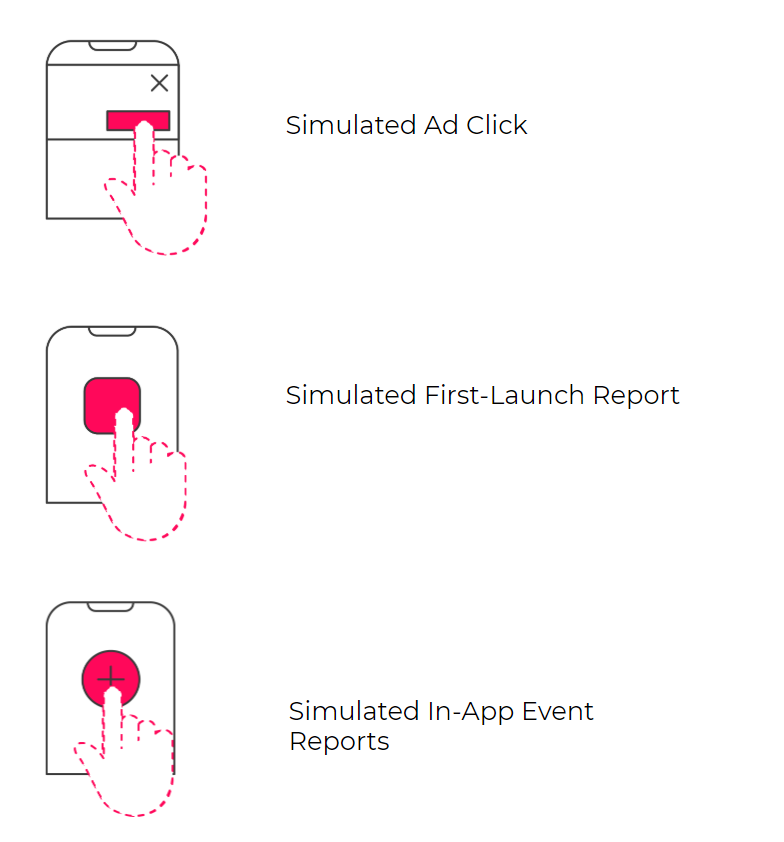
Mobile fraud bots can run off of real mobile devices, but often off servers, attempting to simulate specific tasks, such as ad clicks, installs, and in-app engagement, masquerading as legitimate users.
Another form of bots can be identified as malware located on a user’s device.
These malware programs attempt to generate fake ad impressions, fraudulent clicks and in-app engagement, and could even result in fake in-app purchases without the user’s knowledge.
How do bots work?
Server based bots will operate via emulators (device simulating software) by mimicking an active user’s behavior, interacting with ads, completing app installation funnels and some even reaching as far as a deep in-app event.
These programs constantly refresh their metadata, observe and learn user behavior patterns, applying them in their activity to go under the radar of fraud protection solutions.
IP blacklisting is often applied for blocking server-based bots, however, fraudsters have learned to better hide their activity behind fresh, non-blacklisted IPs, forcing constant updates in blacklists and advanced solutions for fraudulent IP detection.
Device-based bots could use a tactic called SDK mimicking (aka SDK Spoofing), in which App A will try to impersonate App B, sending false click, install and in-app event reports on behalf of App B.
Apps with open source SDKs or ones with low security measurements are more likely to suffer from such attacks, as their SDK is easier to breach, mimic or reverse engineer.
How to block mobile fraud bots?
- Closed source SDKs: Make sure your attribution provider relies on closed source technology for their SDK. Unlike open source SDKs, a closed source code will be significantly more difficult for fraudsters to unpack and simulate, as their code is not exposed openly for anyone to review and reverse engineer. Make sure to review all SDKs used in your app, if some of them apply open source technology (especially attribution SDKs) this could be a security breach.
- SDK security measures, such as hashing or unique tokens help block bot activity in real-time. Using the latest SDK version of your attribution provider will ensure that you have the latest security updates and are up to par with known bot tactics.
- Bot signatures: fraud solutions maintain a real-time bot signature database, automatically blacklisting and blocking all activity from known signatures.
- Identify behavioral anomalies such as high densities of installs that follow identical or programmatic, non-human behavioral patterns. Protect360 applies a proprietary behavioral anomaly detection solution, automatically blocking sources generating such non-human traffic.



