Device ID reset fraud
Device ID reset fraud is a type of fraud that simulates installs from new users. To fake these installs, fraudsters click on ads, install an app, generate in-app engagement, and later reset the device ID of the phone or tablet before uninstalling and reinstalling a given app.
How did Device ID reset fraud come to exist?
For years Apple and Google have been moving towards more a privacy-centric user experience for their respective devices. Device IDs were (and still are) used by both operation systems as a way to better understand users and their journey while anonymizing personal information as well as clicks, installs, etc.
Both OS’s gave users the ability to reset these IDs – an action that had consequences for measurement. If a user chose to reset their ID and then uninstalled and reinstalled an app, the install (and any other actions) would appear to be from a new user.
Fraudsters picked up on the opportunity at hand. To make certain networks looks more desirable, or to simply exhaust the marketing budget of app marketers, they’d reset, uninstall, reinstall, and take actions at scale.
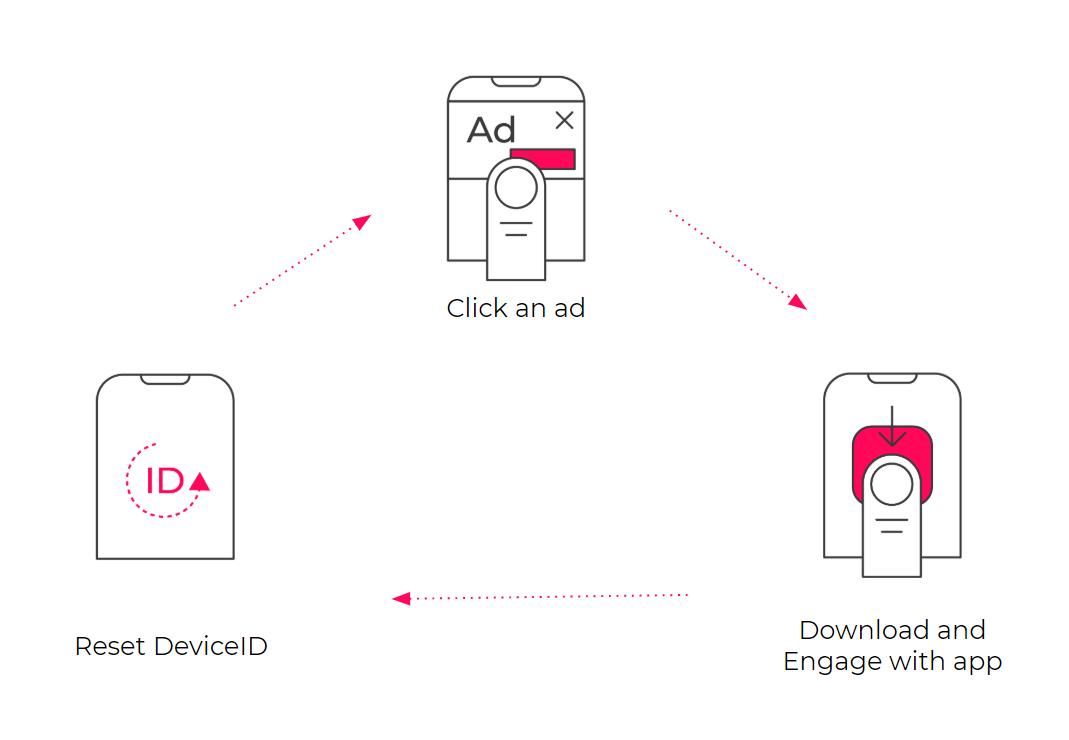
How does it work:
When resetting their device IDs continuously between installs, fraudsters effectively generate significant numbers of “real” clicks, installs, and engagement from new device IDs, bypassing real-time, anti-fraud protection measures.
Pretending to be seemingly legitimate app install activity, the cyclical actions, perpetrated by phone farms, are repeated at scale (sometimes known as reset marathons).
While the app install and engagement activity appears to be real, none of it has any actual value to advertisers or apps’ growth.



