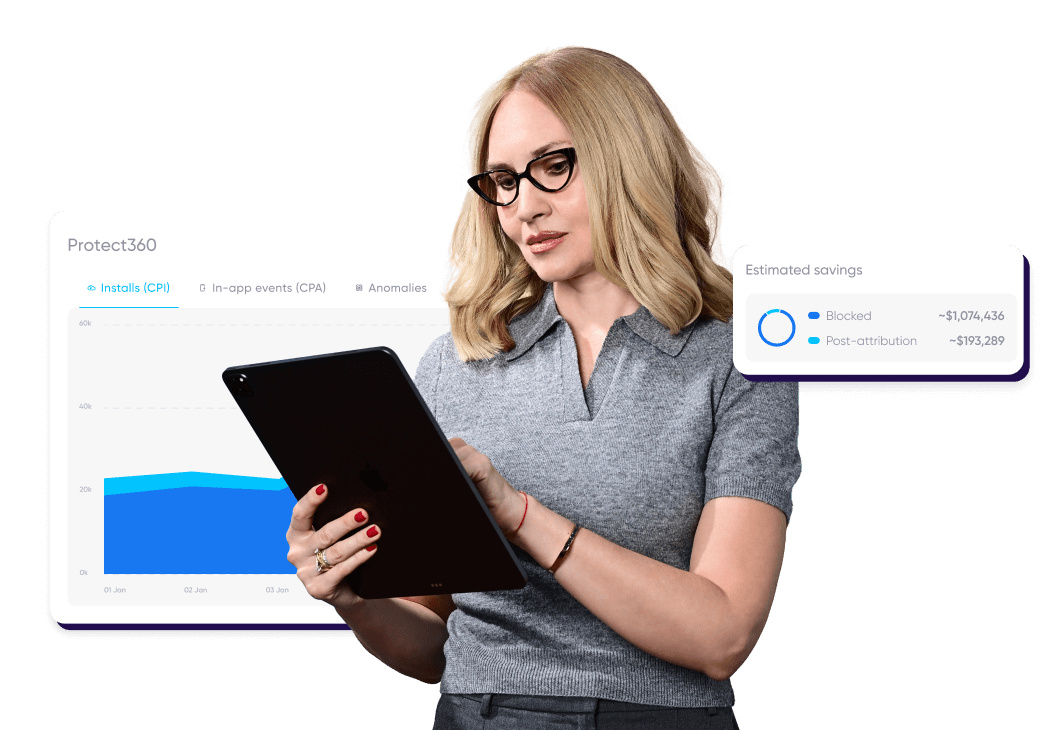
Be ready for anything with multi-layered protection
Mobile ad fraud comes in many forms, and continues to change. We keep you ahead of every threat, and your marketing budget safe, through a real-time, multi-layered approach that includes cluster analysis, personalized validation rules, in-app fraud rules, and post- attribution fraud detection.